The Recon-NG Framework is a powerful tool that allows you to perform automated information gathering and network reconnaissance. Think of it as Metasploit for information collection.
Recon-NG automates a lot of the steps that are taken in the initial process of a penetration test. It has numerous features that allow you to collect user information for social engineering attacks, and network information for network mapping and much more.
You can automatically hit numerous websites to gather passive information on your target and even actively probe the target itself for data.
Anyone who is familiar with Metasploit will feel right at home as the interface was made to have the same look and feel. The command use and functions are very similar. Basically you can use Recon-NG to gather info on your target, then attack it with Metasploit.
INSTALLING RECON-NG
To install Recon-NG, simply download the program from the Recon-ng repository:
git clone https://LaNMaSteR53@bitbucket.org/LaNMaSteR53/recon-ng.git
Then surf to the Recon-ng directory:
cd /recon_ng
and run the program:
./recon-ng.py

Typing ‘help’ will bring up a list of commands:

Now, like Metasploit, you can type ‘show modules’ to display a list of available modules.

Some of the modules are passive, they never touch the target network, while some directly probe and can even attack the system you are interested in.
One tactic used to passively probe network structure is to use the Google search engine to enumerate site sub-domains. You know that there will be a http://www.some_target_name.com but what other subdomains are out there?
You can do a Google search for subdomains using the site: and inurl: switches. Then remove sub-domains (-inurl) that you find so other subdomains will appear. This can take a while to do by hand and can require a lot of typing if the target has a large number of sub-domains.
Recon-NG will do this for you automatically and record what it finds in a database.
Just use the ‘recon/hosts/gather/http/web/google_site’ module. Then ‘show options’ to see what the module requires. This one only requires a target domain.
As in Metasploit just type ‘set domain targetname.com‘. Then just type ‘run‘ and the module will execute as seen below:
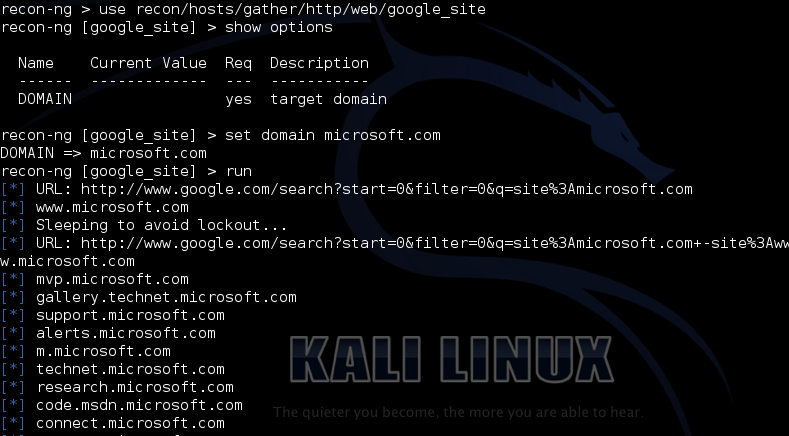
As you can see from the screenshot Recon-NG is enumerating the sub-domains for Microsoft. Within seconds, several of the sub-domains are listed.
All the data collected by Recon-NG is placed in a database. You can create a report to view the data collected. Just type in ‘back‘ to get out of the current module. and then ‘show modules‘ again. Simply use one of the report modules to automatically create a nice report of the data that you have obtained.
Here is a sample of the HTML report:

Sub-domain enumeration is only one module you can run, there are many others to choose from. There are also some that require a program API key like Twitter, Shodan, LinkedIn or Google. Using these you can get specific information from the corresponding sites about your targets.
For example you can search Twitter for tweets from your target or even check Shodan for open systems.
I have just briefly touched on some of the capabilities of Recon-NG. It is really an impressive tool that is well worth checking into.
For more information check out the Recon-NG Wiki page!







