
A recent poll in the UK by the security company LogRhythm revealed that 65% think that Britain should pre-emptively strike countries that pose a cyber threat to the nation. And only 18% of those polled believed that pre-emptive strikes were unjustified.
Britain is hit by up to 1,000 cyber attacks per hour. These attacks are focusing on government sites, corporations, and even the country’s communication network. By why would such a large number believe that first strikes are the correct course of action?
According to the poll, the public in general seems to have lost faith that their private information can indeed be kept private. 41% polled believe that their data stored by companies or the government will be compromised by hackers. And these fears are not unjustified, especially with the rise of hacktivism. Hackers are constantly breaking into big name technology corporations and government sites worldwide and dumping databases to the public.
I agree in taking an offensive stance against cyber attacks. But one problem is the very anonymous nature of the internet. Being attacked in the cyber realm is not like facing another nation on the field of battle. Forces don’t form battle lines and approach in columns. There are no entrenched troops to strike and no supply lines to cut.
It is fairly trivial for a hacker to bounce his attacking traffic through several nations before it reaches the intended target. He could even be using a compromised server in an ally nation (or neutral country) to attack yours. How would you know which nation to strike back at?
Earlier this year a Pakistani hacker group attacked Israeli websites over the Gaza strikes. They changed Israeli DNS settings and pointed major Israeli websites to a defaced website – that was hosted in Texas!
The hacker group set up a server with a legitimate American server hosting company. When they made the DNS change, anyone who surfed to Israel’s Microsoft site or big name social media sites would end up at the server in Texas.
Of course, as soon as the US web hosting company was notified of what was going on, they moved to have the correct DNS settings restored and took down the hosted webpage. Oddly enough, for a short period of time though before it was complete taken down, the hosted website displayed a new message – “Pakistanis Suck!”
Another problem with hacktivism type attacks is that they seem to pull in other groups who respond in kind. So you may have one or two perform web defacements or SQL attacks, then in reprisal two or three other groups attack back in revenge. Which of course spurs more groups into the fray to respond with their own attacks.
Granted these are more nuisance types of attacks, but as Russia’s military is rumored to use the RBN to perform attacks, China or other nations could do the same. And they could be armed with more potent programs like Stuxnet, instead of those that just perform denial of service attacks.
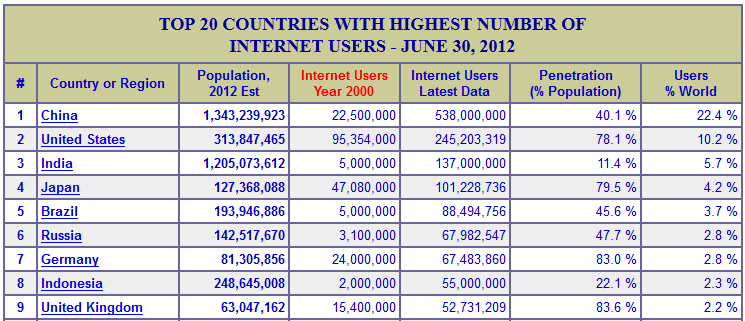
A lot of cyber attacks and cyber espionage attempts do seem to originate from China. By far, China has the most internet users in the world. They have 10 times the users that the UK has and twice as many as the US. The scary part is that the US already has almost 80% of their population online. so far, China is only 40% connected…
At this point they could probably put up 5-10 very talented hackers for every one of ours. Maybe 100 or even 1000 to one for those just running script based attacks or using hacker programs.
Do we really want to get into a tit-for-tat battle with them?
Something must be done, and now. Any attacks against foreign nations would have to be covert. Chances our that allied forces already have a good hold on foreign networks and communication systems.
The US cyber command was formed from initial work by the NSA. According to Richard Clarke’s book “Cyber War: the next Threat to National Security” the NSA has already compromised many foreign networks:
“Although not authorized to alter data or engage in disruption and damage, NSA thoroughly infiltrated the Internet infrastructure outside the U.S. to spy on foreign entities.”
But the NSA did not have legal authority to actually attack in times of war. US military forces were folded in with the NSA to give it the legal authorization needed to attack foreign cyber space. Thus creating Cyber Command.
The US is allegedly the top in offensive cyber power, but obviously is far lacking in defense. The UK suffers from the same weakness. This past summer, Jonathan Evans, the head of MI5 claimed that one attack alone caused a London based company about $1.3 Billion.
The question is then, how do we perform critical pre-emptive offensive strikes without being crippled ourselves by a counter attack?






