You have a remote shell to a Windows box in Metasploit, very cool, but what can you do? Granted Metasploit is loaded with features, options and tons of post modules (which are all amazing by the way), but what if you want to do something a bit more custom? Say, like adding custom pop-ups and even voice, but you have no clue about programming in Ruby.
How about PowerShell?
Let me start this out by saying I am no programmer. Sure I have futzed around with various languages over the years, and even supervised programmers at a couple jobs – but trust me, I am not a programmer. Secondly, I never would have been able to do this without one of the Metasploit gods – Mubix over at Room362.com. Thanks Mubix!
Talking with a friend about exploit capabilities, we came up the thought that wouldn’t it be cool if when a machine was exploited during a red team pentest, if it would pop up a Windows error message on the screen saying, “Knock, Knock Neo.” You know, from the Matrix movie.
And wouldn’t it be cool if you could get the computer to speak to said victim in a woman’s voice saying the same thing? What if, as long as we are custom creating our Matrix-ish payload, we also wanted to pop up a picture on the target system of the green text filled Matrix screen? I mean wouldn’t that be cool too?
Well, with PowerShell, you can!
If you look at Mubix’s “Powershell Popups + Capture” article, you can see the step-by-step process that we will follow.
Create a text file containing the Powershell commands, I used something like this:
$shell = New-Object -ComObject “Shell.Application”;
$shell.minimizeall();
Start-Sleep -s 2;
[System.Reflection.Assembly]::LoadWithPartialName(“System.Windows.Forms”);
[System.Windows.Forms.MessageBox]::Show(“Knock, knock, Neo.” , “Status” , 2);
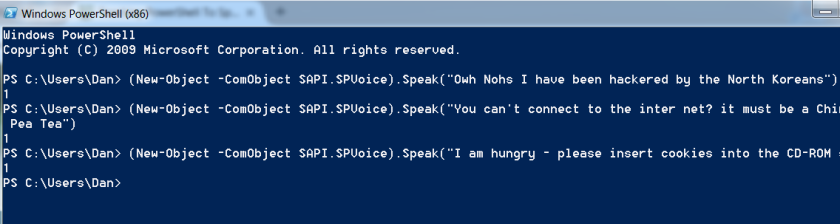
(New-Object –ComObject SAPI.SPVoice).Speak(“Knock, Knock Knee Oh, the Matrix has you!”);
c:\test\matrix.jpg;
The first two lines allow the script to clear the user’s screen by minimizing all open windows. We then pause the script for a couple seconds for dramatic effect. The next two lines pop up a Windows (Abort, Retry, Ignore) message box with the movie message, “Knock, Knock Neo.”
Once the user clicks on one of the message box buttons, the script calls the Windows built in text to speech capabilities to audibly speak the same message out of their speakers. Sometimes the words don’t come out exactly like they should so you need to help the Windows voice API by using slightly different, but similar sounding words (ex. “Knee Oh” instead of “Neo”).
The final command opens a Matrix .jpg file that we would need to have already uploaded to the system via the Meterpreter upload command. (Pick a big one that fills the screen!)
We need to take the text file and encode it as Mubix’s site shows:
Then run the following command in our remote shell, adding in the encoded text stream above:
powershell -ep bypass -enc <Paste in the Encoded Text>
And that is it!
One more step that would make this even more creepy (or visually convincing in a red team pentest) would be to use Meterpreter’s built in webcam capability to first snap a picture of the remote user at his computer, upload that picture to their system in place of the matrix.jpg, and then run the command for a more personalized message from “the Matrix”!
Best defense against these types of attacks is to never, ever open or run unexpected files or attachments in e-mails. Never use a USB drive that you find laying around your company. Avoid public Wi-Fi when possible. Finally, always use a script blocking program on your internet browser.