You can now quickly detect the OpenSSL-Heartbleed vulnerability very quickly on a network using the ever popular nmap command, and with the latest modules from Metasploit you can quickly see the exploit in action.
For this tutorial I will be using a WordPress server and Kali Linux running in two separate VMWare virtual machines.
For a vulnerable server, I used one of Turnkey Linux WordPress VMs. There are security updates available for Turnkey’s WordPress, but during the VM setup, and for this tutorial, I purposefully told the VM NOT to install the security updates so I could test for the OpenSSL vulnerability.
Once the WordPress VM was configured (just answer a few simple questions) I then fired up my Kali Linux VM.
Nmap has created a Heartbleed script that does a great job of detecting vulnerable servers. The script may not be available in your version of Kali, so you may have to manually install it.
Detecting Exploit with Nmap
If the Open-Heartbleed script is not already included in your nmap install, you will need to manually install it.
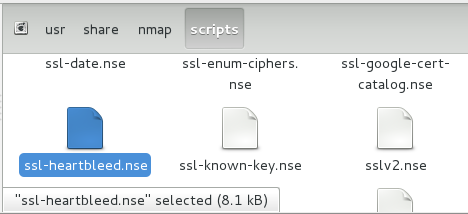
This is pretty easy, just visit the OpenSSL-Heartbleed nmap Script page, copy and save the nmap nse script file to your nmap “scripts” directory as seen below:
You will also need the nmap “tls.lua” library file, save this to the nmap “nselib” directory as seen below:
That is it, we can now use the heartbleed script in nmap to detect vulnerable systems.
To use the command the syntax is:
nmap -sV --script=ssl-heartbleed <target>
All we need to plug in is the IP address of our target test WordPress site, 192.168.1.70 in this instance:
And if the target machine is vulnerable we will see this:
State: VULNERABLE
Risk Factor: High
Exploiting with Metasploit
Now that we know we have a vulnerable server, we can use the latest Metasploit OpenSSL-Heartbleed module to exploit it. (Note: you can use the module to detect vulnerable systems also)
Update metasploit to get the latest modules. Just type “msfupdate” at a Kali command prompt:
Now run “msfconsole” to start Metasploit and you will be presented with the Metasploit console:
Next search for the heartbleed modules:
Notice there are two, we will just be using the scanner.
Type, “use auxiliary/scanner/ssl/openssl_heartbleed“:
We are just going to set two options, “set VERBOSE” to true and we need to “set RHOSTS” to our target IP address as seen below:
And finally, just “run” the exploit:
If you click on the picture above, you will see that Metasploit communicated with the server and was able to pull random data from the server’s memory.
The important thing to note here is that it pulls random data from memory. There is no guarantee that you will find account credentials, session cookie data or critical data every time you run this. But the danger is in the fact that it could display sensitive data.
Thus the best practice (if you haven’t already) is to check your systems for the heartbleed vulnerability and patch them immediately. After the systems are patched change any passwords on the effected machines.
As always, never run security scans or checks on systems that you do not own or have approval to scan.
If you enjoyed this tutorial and want to learn more about Kali Linux and Metasploit, check out my latest book on Amazon, “Basic Security Testing with Kali Linux“.