As usual, I like to take sanitized lists (user account information stripped) of public password dumps and analyze them for password strength and patterns. Recently the subscriber database for Journal News, Lower Hudson Valley was allegedly hacked and was published publicly online.
The dump had user account passwords stored in MD5 hashes. So they needed to be cracked before they could be analyzed.
There were about 10,000 user accounts leaked in the dump. Many had duplicate password hashes, so the duplicates were removed. I took the password hashes that had not been cracked (some were already cracked in the dump) and ran them through an MD5 hash cracker. In a couple hours I was able to retrieve just over 85% of the passwords.
In effect there were 8,361 unique hashes. I was able to retrieve 7,148 in a fairly short amount of time. I then took the cracked passwords and ran them through Pipal, the password analysis program.
Here are the results from Pipal
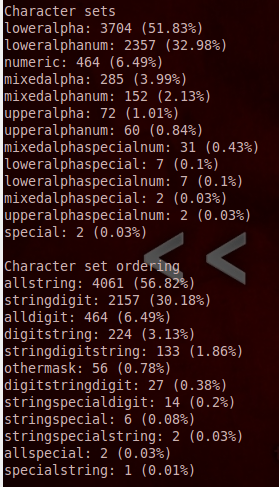
Top 10 words and base words used:
Very interesting as there are 10 passwords that are almost ALWAYS in the top ten and none of them were in this list. Okay, “password” was used as a base word, but other than that these are all new.
Let’s take a look at the password lengths:
A whopping 80% of the passwords were 8 characters or less, and over 50% of the passwords only used lowercase letters!
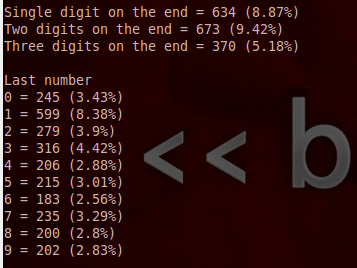
A common practice is that users will use a word and stick a number or numbers on the end to “make it more secure”. About 25% of the passwords in this list used 3 or fewer numbers at the end of the password.
And only a few passwords used the year in their password.
Overall the users in this case seemed to use very simple passwords – mostly lower case passwords with some numbers mixed in. Using long complex passwords would have made these passwords much harder to crack.
Increasing the password length and using a mix of upper and lower case letters, numbers and special characters dramatically increases the cracking times.